Wireshark Dissector for Samsung remote protocol
There is a Wireshark[1] dissector for Samsung SmartTV remote control protocol. The dissector's sources and distribution are available at bitbucket[2]
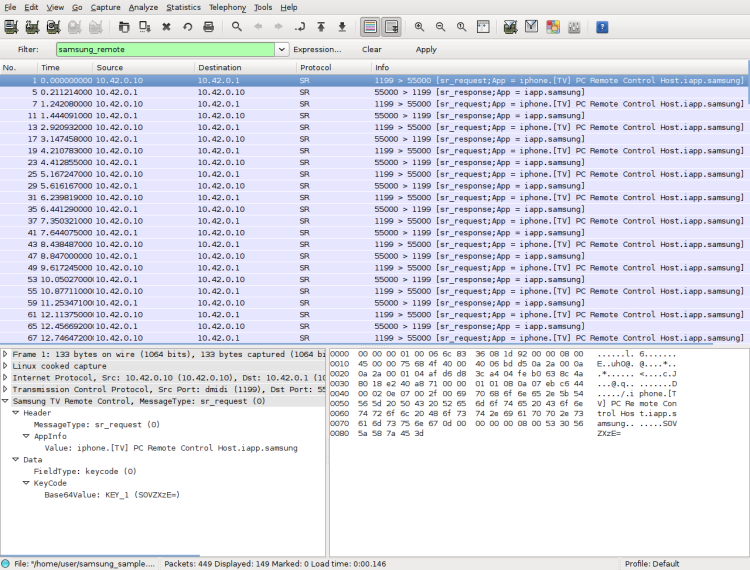
This dissector allows to filter wireshark captures and decode remote control packets that are sent to the TV by WiFi and packets that are sent from TV to remote control unit. This dissector is based on WSGD[3] - Wireshark plugin which allows simple declarative creation of your own dissectors for custom protocols.
To install the dissector to your wireshark installation you need to do the following actions:
- Download[4] version of WSGD that matches your wireshark version and machine architecture and put it to your wireshark plugins folder
- Unzip dissector files[5] or one of the folders described here[6] (e.g. /usr/lib/wireshark/libwireshark0/plugins/).
To see dissector in action yo could do this:
- Run wireshark with installed dissector.
- Download sample capture[7] file and open it in wireshark.
- Type samsung_remote in the filter field;
- See filtered Samsung Remote packet
- Click one of packets marked with SR protocol and see decoded packet data
Screenshot of wireshark with sample cature and working dissector: